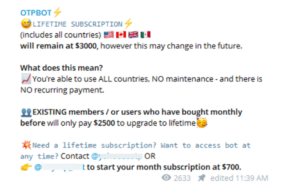
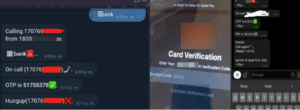
Two-factor authentication (2FA) is a commonly used tool to add an extra layer of security and prevent unauthorized login of online accounts. Many websites now leverage one-time passwords (OTP) to authenticate a login and verify the user’s identity. Not surprisingly, cybercriminals and fraudsters have consistently developed various techniques to bypass and defeat 2FA. OTP bot services have become increasingly popular with cybercriminals and fraudsters in recent months. OTP bots communicate automatedly with victims, attempting to trick them into providing information required for account takeover. These services use bots to initiate phone calls to the victims and solicit sensitive information such as 2FA codes, account PINs, and other PII. For the most part, these bot services are provided as a service, and they are available in various underground communities and telegram channels. Any threat actor willing to pay can get immediate access to these bots.
OTP Bots Are a Growing Threat: What Financial Institutions Need to Know