
Email Cybersecurity Threats: How to Protect Yourself and Your Company
$5,300,000,000,000 … That’s how much cybercriminals have siphoned from businesses and consumers worldwide through business email compromise (BEC) and email account compromise (EAC) scams since 2013, according to the Internet Crime Complaint Center (IC3). The FBI noted that these scams have increased 136% worldwide from December 2016 to May 2018.
BEC and EAC scams are very similar in how they attack their victims, causing companies to pay more attention to their cybersecurity. The biggest difference is that BEC scams target companies, while EAC scams are directed at the victim’s personal accounts. Regardless, both are equally threatening to financial cybersecurity.
How Do These Scams Work?
There are three basic stages to a BEC/EAC scam:
- Stage 1 – Compromising victim information and email accounts
- Stage 2 – Transmitting fraudulent transaction instructions
- Stage 3 – Executing unauthorized transactions
Stage 1 – BEC/EAC scams can be completed through a simple email exchange with a fraudulent look-alike email or with a more advanced email phishing scheme. Through social engineering or malware, fraudsters attempt to compromise a legitimate business e-mail account. If they cannot compromise an email, the scammer spoofs a valid email address by inserting a character such as a “0” (zero) in place of an “O” (capital letter O), making the fake email look realistic.
Social engineering is the use of deception to manipulate individuals into giving out personal or confidential information, either in-person or through digital channels. The fraudsters monitor and study their selected victims prior to initiating the scam. This can be everything from diving deep into the victim’s social media accounts or physically infiltrating a business to gain information. The growth of the internet and social media has made social engineering significantly easier and less time-consuming. Now, instead of visiting a physical location, the scammers can get most of the needed information through a simple web search. According to the IC3, “The subjects are able to accurately identify the individuals and protocols necessary to perform wire transfers within a specific business environment. Victims may also first receive ‘phishing’ e-mails requesting additional details regarding the business or individual being targeted (name, travel dates, etc.).”
In other instances, victims of the BEC scam report being targeted by ransomware cyber intrusions immediately preceding a BEC incident, usually through a more complex phishing scam. A victim receives an e-mail from a seemingly legitimate source, such as a coworker, friend or vendor, that contains a link. When the victim clicks the link, they unknowingly download malware, which gives the criminals access to confidential or secure internal information. These malware programs allow the attacker to infiltrate the company’s email system or victim’s email account and learn their normal procedures for money transfer by reading through sent items folders.
Stage 2 – Once the criminals have the information they need, they send the payment information. Since wires are a quick international transfer vehicle, most BEC/EAC scams request wire transfers. According to the 2017 AFP Payments Fraud and Control Survey, checks are the second-most requested payment vehicle. ACH credits and corporate/commercial credit/debit cards are tied as the third-most frequent payment vehicle.
Stage 3 - Often, the victim is asked to keep the transfer confidential and there is an element of urgency associated with the payment or transaction. Criminals are taking these scams one step further now, often calling the victim to follow up on the wire request, giving the transaction more perceived legitimacy.
More advanced crime rings behind these scams regularly use “money mules” to move the transferred funds, making it harder for financial institutions to detect. Sometimes, the scam victims themselves are recruited as innocent money mules. Fraudsters also recruit mules from “work from home” postings or romance schemes. The mules receive the fraudulent funds in their personal accounts and are then directed by the fraudster to quickly transfer the funds to another financial institution account, usually outside the U.S. Most payments end up in Asian financial institutions with China and Hong Kong leading the way. The IC3 reported, however, that 113 other countries have also been recipients of these transfers.
So what’s the difference?
BEC scams target a business that regularly performs wire transfer payments or works with foreign suppliers. Victims range from small businesses to large corporations and deal in a wide variety of goods and services, indicating that every business is at risk.
It is important to note that not every BEC scam contains a payment element. The criminals might also be asking for confidential information in the form of Personally Identifiable Information (PII) or Wage and Tax Statement (W-2) forms.



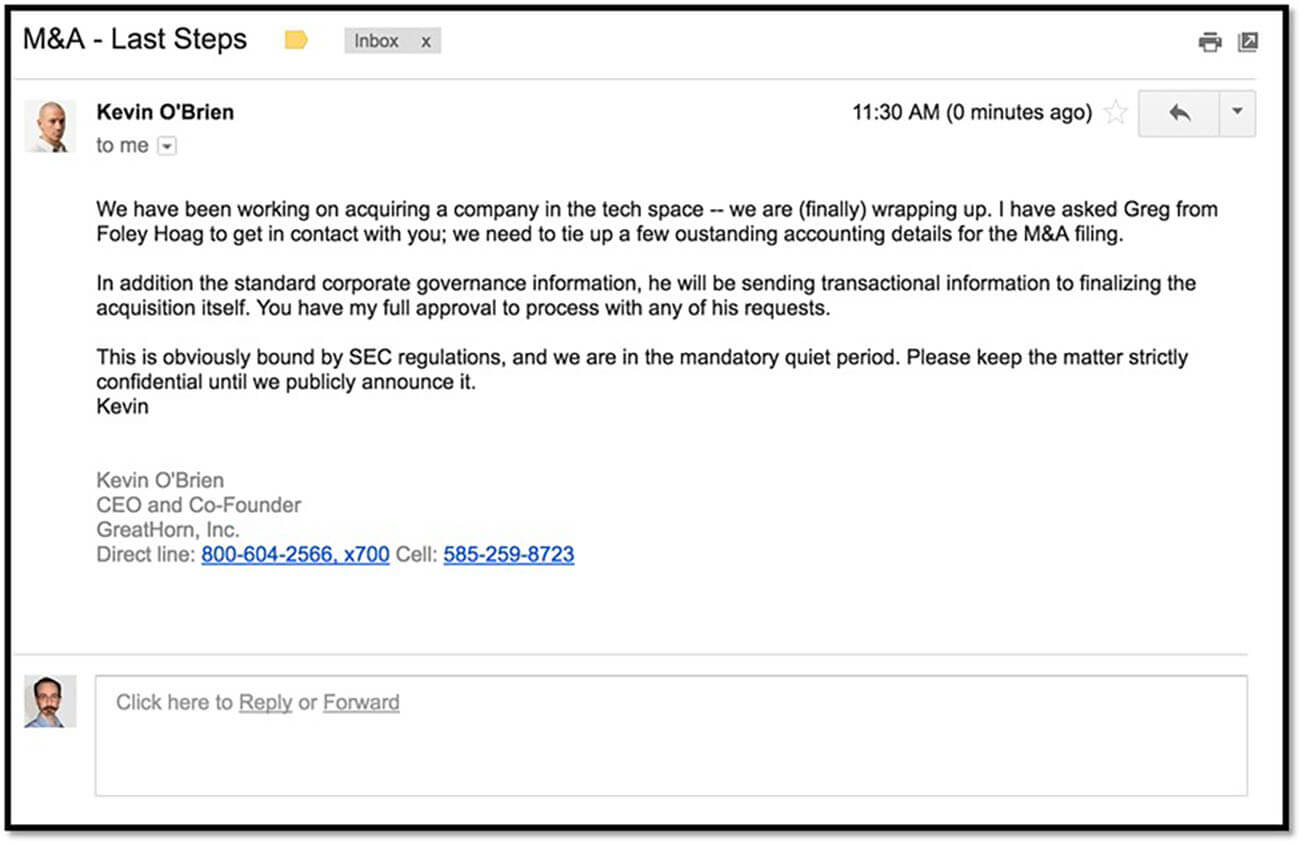 This example highlights two common components of a BEC phishing email: an element of urgency and a request to keep the transfer confidential.
This example highlights two common components of a BEC phishing email: an element of urgency and a request to keep the transfer confidential.